How Does Blockchain Security Work?

Team Fueler
30 Sep, 2022

Cybersecurity has become a challenge for businesses worldwide due to internal threats and vulnerable networks. For example, an insider threat allows unauthorized access or abuse of information inside the organization causes exposure to hackers. Such cyber-attacks can be rescued through Blockchain security. So, what is Blockchain?
Blockchain has a distributed structure, with each transaction visible to everyone within the network. Every Blockchain gathers data in groups known as blocks. Once a block is filled, it is linked to a new block forming a chain.
Each data transaction or exchange is transmitted through a network where members validate it and the distributed ledger recorded it. However, can it solve the problem of internal threats or other such cyber-attacks?
According to Forbes, 93% of companies have vulnerabilities in their network that hackers can exploit to steal sensitive information. Blockchain-based security can help you create a strong network that is hard to break. Here we will understand how Blockchain works and secures the data.
First, let us understand what Blockchain is.
Blockchain: A decentralized ledger! [What is Blockchain?]
Think of an intelligent excel sheet with many copies across locations, and each data entry needs validation from the computer that has a copy; Blockchain works on a similar principle. It is a decentralized ledger with all the transactions copied to each computer in the network. Therefore, there is a record of all the data exchanged.
A chain of new and old blocks provides full access to all data while keeping its integrity intact. Unlike the conventional approach with a single point of failure, decentralized blockchain technology, supported by decentralized exchange software development, helps reduce the risk of data leakage.
Key takeaways
- It is a shared database, which means there is an openness to transmitted data and a reduced risk of data leakage.
- No single point of failure as multiple copies of data are created and stored across the network.
- Scalability of data is not an issue, as you can create multiple blocks without compromising on security.
- Every network member must validate a data transaction, its source, and its legitimacy, ensuring no single-handed transaction management control.
- All the transactions are immutable, meaning internal threats are minimal, and hackers can't change the credentials to access data.
How does Blockchain security work?
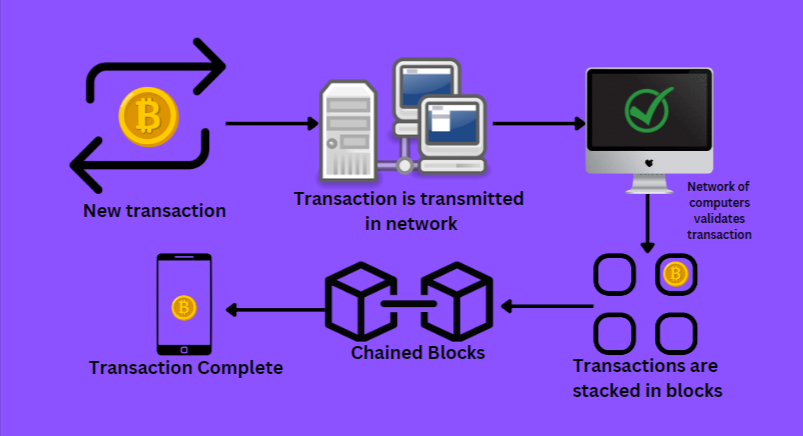
Blockchain's working principle is decentralization and immutability. In other words, data exchanged on the network should be recorded, validated, and no one can change it. So let us understand how Blockchain works through a systematic flow of transactions.
- A new transaction occurred and is transmitted into the network.
- A peer-to-peer network of computers scattered worldwide solves math equations to confirm the validity of transactions.
- Validated transactions are grouped in a block.
- These blocks are chained together to form a record or ledger of all the transactional history.
So, how does Blockchain technology ensure security?
Blockchain security at work!
Imagine an e-Commerce company that owns data centers with more than 10,000 servers. It stores users' financial information on the servers and needs to keep it secure according to the Payment Card Industry Data Security Standard (PCI DSS).
Now conventionally, hackers can use vulnerabilities in the network or a backdoor to access sensitive data from the servers. Nevertheless, with Blockchain, the entire scenario changes. In addition, Blockchain security vulnerabilities are harder to find because each transaction is recorded and validated.
Therefore, hackers don't have the leverage of changing a few codes or credentials to gain root access to the server's admin. Blockchain allows the data stored in a database to spread among various nodes in the network. Several copies of the data create a secure environment for the information exchange.
Even if a hacker can get hold of Blockchain security vulnerability and change the data in one node, other nodes will not alter information. Therefore, data remains immutable and secure.
Nevertheless, are there any vulnerabilities in Blockchain security? Let us explore!
Blockchain security vulnerabilities
There are two types of Blockchain security based on types of networks, public and private. The difference between public and private Blockchain security is data access capabilities. Blockchain private or public networks are defined by members' privileges on accessing the information.
Public Blockchain networks allow users to join the network keeping them anonymous and open in characteristic. It means any user can participate without any specific privilege.
On the other hand, a private Blockchain network allows users to access data only after they are authenticated. They confirm the identity and access privilege of the member before adding them to the network.
However, most Blockchain security vulnerabilities are not inherent. There are specific drawbacks to the Blockchain approach, which can lead to vulnerabilities.
51% attacks
It is one of the most significant attacks, as hackers can seize control of the system. A 51% attack takes place an organization or a single hacker gathers more than 50% of the hash rate to control the system. Further, attackers can change transaction orders in the ledger and prevent validation. They can even reverse earlier transactions, which can affect users' financial accounts.
However, you can improve Blockchain security for 51% attacks by monitoring the mining pools and ensuring a higher hash rate.
Phishing attacks
Phishing attacks are hard to execute on Blockchain networks. However, attackers leverage social engineering tactics to gain access to the credentials of miners. So, with access to mining resources, they can access critical information regarding the transactions in the network.
The best way to improve security for your user credentials is to use a secure browser and avoid opening emails from unknown sources.
👨💻 Access the collection of Google Search Tips & Tricks for Free
Routing attacks
A transaction is initiated and transmitted to a secure network at the outset of a Blockchain. Now, if a hacker can access the transaction data while it is transmitted, such an attack is called routing. Here hackers can access users' financial data and extract cryptocurrencies without users' knowledge.
The best way to secure your transactions from routing attacks is to use data encryptions and implement a routing protocol with SSL certificates.
Endpoint vulnerabilities
The vulnerability of endpoints is a significant concern for Blockchain security. Users use devices like mobile phones and computers to access the Blockchain network. These devices can be the gateway that hackers use to attack the network and access users' credentials.
The best way to avoid such attacks is to ensure you do not save Blockchain keys on your personal computers or mobile devices.
Fake network nodes
Another significant Blockchain security vulnerability you must remember is the Sybil attack. It is an attack where hackers create several fake nodes to create a majority consensus for transactions. Hackers can disrupt the chain and affect the entire ledger.
If you want to avoid such attacks, you can use secure consensus algorithms and monitor the node's behavior.
Is Blockchain The Future Of SSL Certificates?
Secure Socket Layer or SSL is a cryptographic encryption-based protocol that enables secure communication between the browser and the server. Blockchain integration with SSL/TLS technology has a bright future due to enhanced data security.
SSL certificates ensure that data stays anonymous between the browsers and server. On the other hand, Blockchain ensures that data is secure through constant information validation by all the network members.
Integrating SSL and Blockchain can help secure data transfer across different websites. Especially SSL certificates can help you reduce risks involved with Blockchain endpoint vulnerabilities. Users can buy SSL certificates and install them on their server to ensure that transaction transfer to the Blockchain network is secure.
Conclusion
Securing the browsers is important to ensure the user's credentials are safe. Especially for e-Commerce, businesses need to ensure that users' financial transactions are secure. SSL certificates can help to ensure security that is paired up with Blockchain technology; it can do wonders. You need to be mindful of the Blockchain security vulnerabilities, and yet if you follow some best practices, BOCA can be best for data security.
Special thanks to Ken Smith for writing this blog.
If you are a freelance developer, you can use the #1 portfolio tool for developers to land high-quality clients and 10x more money. Showcase your work beautifully and professionally on Fueler. Create your profile on Fueler today.